Ask questions which are clear, concise and easy to understand.
Ask QuestionPosted by Sazid Khan 5 years, 5 months ago
- 0 answers
Posted by Ravi Yadav 5 years, 5 months ago
- 1 answers
Gaurav Seth 5 years, 5 months ago
| Basic | Primary memory is directly accessible by Processor/CPU. | Secondary memory is not directly accessible by CPU. |
| Altered Name | Main memory. | Auxiliary memory. |
| Data | Instructions or data to be currently executed are copied to main memory. | Data to be permanently stored is kept in secondary memory. |
| Volatility | Primary memory is usually volatile. | Secondary memory is non-volatile. |
| Formation | Primary memories are made of semiconductors. | Secondary memories are made of magnetic and optical material. |
| Access Speed | Accessing data from primary memory is faster. | Accessing data from secondary memory is slower. |
| Access | Primary memory is accessed by the data bus. | Secondary memory is accessed by input-output channels. |
| Size | The computer has a small primary memory. | The computer has a larger secondary memory. |
| Expense | Primary memory is costlier than secondary memory. | Secondary memory is cheaper than primary memory |
| Memory | Primary memory is an internal memory. | Secondary memory is an external memory. |
Posted by ♌ Hire 5 years, 5 months ago
- 1 answers
Posted by Ashish Jha 5 years, 5 months ago
- 1 answers
Gaurav Seth 5 years, 5 months ago
Microsoft is a leading global vendor of computer software; hardware for computer, mobile and gaming systems; and cloud services. Microsoft's corporate headquarters is located in Redmond, Wash., and it has offices in more than 60 countries.
Company origins:
Microsoft's roots go back at least as far as 1975, when the first commercially available personal computer appeared on the cover of Popular Electronics magazine. The Altair 8800 was a rudimentary system, but it found a market for home-based computers and created a new demand for software to use with these systems.
Posted by Omkar Jadhav 5 years, 6 months ago
- 1 answers
Posted by Rock Blaster Sagar 5 years, 6 months ago
- 1 answers
Kartik Yadav 5 years, 5 months ago
Posted by Neelam Shaktawat 5 years, 6 months ago
- 1 answers
Yogita Ingle 5 years, 6 months ago
An organization performs all the activities through proper communication. To perform the organizational activities smoothly and efficiently, effective communication plays a vital role. Effective communication makes the receiver understand the meaning of the message as per the intention of the sender. It makes the receiver see and feel as the sender does. The effective communication plays an important role for the successful operation of the organization. There are a number of barriers to effective communication. These barriers are the blockage, breakdowns, and disruption in the flow of the message. Due to these barriers, the receiver cannot understand the meaning of the message as per the intention of the sender. These barriers create problems in responding the message and carrying activities as per the intention of the sender. The barriers to effective communication results due to the following reasons:
- If the symbols used in the message are not correctly understood by the receiver.
- If the information is manipulated as per the interest of the sender.
- If the message is to be transmitted to a long distance.
- If the sender uses technical and difficult words in the message.
- If the sender uses long and complex sentences in the message.
Posted by Omkar Yadav 5 years, 6 months ago
- 1 answers
Yogita Ingle 5 years, 6 months ago
Primary memory is the main memory of the computer system. Accessing data from primary memory is faster because it is an internal memory of the computer. The primary memory is most volatile which means data in primary memory does not exist if it is not saved when a power failure occurs.
Two types of Primary Memory are:
- RAM: Random access memory which is also known as RAM is generally known as a main memory of the computer system. It is called temporary memory or cache memory. The information stored in this type of memory is lost when the power supply to the PC or laptop is switched off.
- ROM: It stands for Read Only Memory. ROM is a permanent type of memory. Its content is not lost when the power supply is switched off. The computer manufacturer decides the information of ROM, and it is permanently stored at the time of manufacturing which can not be overwritten by the user.
Posted by Varshika Srivastava 5 years, 6 months ago
- 1 answers
Gaurav Seth 5 years, 6 months ago
Definition: The computer is an electronic device. It is known as an electronic device because it runs through electricity. It takes input, processes it and gives desired results. The results of the computer system are also known as output.
<center>Computer characteristics
</center>- Speed: The computer is a much faster device. A computer machine can solve very complex problems faster than a person. It gives results within a second. Now a day, the computer can solve not only a single problem but also multiple problems within very less time.
- Data Storage: A computer system can store a large amount of data for a long time period. The data can be store in internal as well as external devices. The internal device of data storage is Hard disk and external storage devices are Pen drive, External Hard disk, etc.
- Accuracy: Computers can generate reliable results with high computational speed. If the input is right then only the appropriate output will be generated. The computer never gives inaccurate results; if results are inaccurate it means inputted data was erroneous.
- Versatility: A computer is a versatile machine that can perform different types of jobs with the same accuracy rate.
- Diligence: Computers never get tired. As humans get tires when he works regularly but the computer can perform tasks over and over again, with the same outcome, and it does so without tiring.
- No IQ: It performs a task that is exactly as directed by the user because it does not have its intelligence.
Reliable: Consistency refers that a computer is a reliable machine, as it always gives consistent results.
Posted by Krish Chauhan 5 years, 6 months ago
- 2 answers
Yogita Ingle 5 years, 6 months ago
The full form of CPU is the Central Processing Unit. The CPU socket is a particular section where the CPU is mounted inside the motherboard to perform other outputs and inputs of the system. The CPU’s known as the brain of a computer. It performs all the basic logical and arithmetic operations activities and transmits the commands and programs of the computer. The term CPU is normally used to refer to a processor that consists of the arithmetical logical unit
and control unit.
CPU = ALU + CU
Where
ALU – Arithmetical Logical Unit
CU – control unit
Posted by Devraj Kumar 5 years, 6 months ago
- 1 answers
Meghna Thapar 5 years, 6 months ago
Communication is simply the act of transferring information from one place, person or group to another. Every communication involves (at least) one sender, a message and a recipient. These include our emotions, the cultural situation, the medium used to communicate, and even our location. Communication provides the information individuals and groups need to make decisions by transmitting the data needed to identify and evaluate choices. Thus communication helps to facilitate decision making.
Posted by Jinu Puthran 5 years, 6 months ago
- 4 answers
Gaurav Seth 5 years, 6 months ago
-
Locate the file or folder by using Windows Explorer.
To do so, right-click Start and choose Open Windows Explorer and then browse to locate the file you want to delete.
-
In Windows Explorer, right-click the file or folder that you want to delete and then choose Delete.
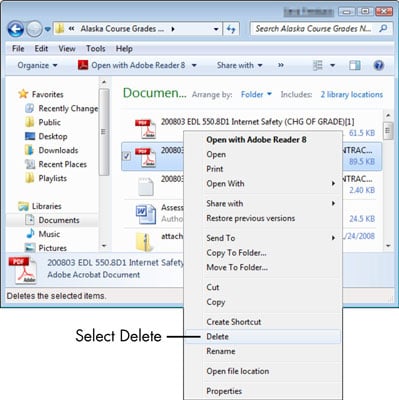
The Delete File dialog box appears.
-
Click Yes to delete the file.
Instead of right-clicking and choosing Delete from the menu that appears earlier, you can press the Delete key on your keyboard.
Dev Prakash 5 years, 6 months ago
Aman Kumar 5 years, 6 months ago
Posted by Rakhi Agrawal 5 years, 6 months ago
- 0 answers
Posted by Bhavya Watvani 5 years, 6 months ago
- 1 answers
Gaurav Seth 5 years, 6 months ago
Single-level directory structure
Single level directory structure has only one directory which is called the root directory. The users are not allowed to create subdirectories under the root directory. All the files created by the several users are present in the root directory only.
Posted by Bhavya Watvani 5 years, 6 months ago
- 0 answers
Posted by Jitendra Singh 5 years, 6 months ago
- 1 answers
Agnes Jimmy 5 years, 6 months ago
Posted by Sazid Khan 5 years, 6 months ago
- 1 answers
Mr. Sinha 5 years, 6 months ago
Posted by P-Astro1982 Sharma 5 years, 6 months ago
- 1 answers
Jitendra Singh 5 years, 6 months ago
Posted by Krishnav Goswami 5 years, 6 months ago
- 1 answers
Posted by #Kavya Goenka 5 years, 6 months ago
- 2 answers
Yogita Ingle 5 years, 6 months ago
Stands for "Garbage In, Garbage Out." GIGO is a computer science acronym that implies bad input will result in bad output. Because computers operate using strict logic, invalid input may produce unrecognizable output, or "garbage."
Posted by Vaibhav Thakur 5 years, 6 months ago
- 2 answers
Posted by Muskan Sahu 5 years, 6 months ago
- 2 answers
Posted by Kumar Sudhi 5 years, 6 months ago
- 0 answers
Posted by Yã Mí Kú 5 years, 6 months ago
- 5 answers
Madhusmita Sahu 5 years, 6 months ago
Gaurav Seth 5 years, 6 months ago
A one-time password (OTP) is an automatically generated numeric or alphanumeric string of characters that authenticates the user for a single transaction or login session.
OTP is a string of characters or numbers automatically generated to be used for one single login attempt. OTP, One Time Passwords in full, can be sent to the user’s phone via SMS orPush messaging and is used to protect web-based services, private credentials and data. OTP’s will minimize the risk of fraudulent login attempts and thus the risk of stolen data. OTP’s come in all shapes and sizes, but always add an extra layer of authentication.
Posted by Anmol Dwivedi 5 years, 6 months ago
- 3 answers

myCBSEguide
Trusted by 1 Crore+ Students

Test Generator
Create papers online. It's FREE.
CUET Mock Tests
75,000+ questions to practice only on myCBSEguide app
 myCBSEguide
myCBSEguide